waaa.. new release is coming.......
 If there are multiple partitions make sure you have saved everything off them since they might each have different drive letters (i.e. “D:” or “F:”). Then repeat the above step for each of them. If you only want to format one partition that is OK and you can continue to the next step without deleting the other partitions.
If there are multiple partitions make sure you have saved everything off them since they might each have different drive letters (i.e. “D:” or “F:”). Then repeat the above step for each of them. If you only want to format one partition that is OK and you can continue to the next step without deleting the other partitions. | Download the Startup Diskette Creator |
We all know about anti-virus software these days. I guess you have read my comparative study on anti-virus software too. If in case you haven't, here it is. While writing on that article I realized I have been rather superficial on the most important part of an anti-virus column and that is not WHAT cures the disease. Its about HOW they do it. Today let's find out how they actually work.
After a lot of study, I came to know about mainly four different algorithms used by today's anti-virus software to detect viruses:
None of them are individually perfect. However in combination they often prove to be a formidable opponent to any current viruses, trojans and more. Moreover some of the techniques also protect your computer against future viruses.
Most of the old viruses and some new viruses and trojans have a recognizable pattern or signature (sequence of bytes) which anti-virus software looks for. Anti-virus software has a library of signature against which it matches the applications, boot sectors and other possible locations of infection. If it can detect a match it will then signal the end-user with the virus details and location where it was found. Anti-virus software's update these signatures at regular intervals. Unfortunately mutating and polymorphic viruses evade simple signature detection by continuously changing their code. They are detected by advanced techniques discussed below.
Signature detection is simple and fast. Anti-virus software can look for virus signature in large number of files in a very short period of time. This is what makes it a popular option with anti-virus vendors.
Virus creators today mostly code polymorphic viruses which changes the code, while retaining the functionality, thereby evading signature detection algorithm. There are virus toolkits available for free which allows even a script-kiddie to code a polymorphic virus with minimal expertise. This can be a useful technique only in conjunction with other techniques but not alone. It is in some ways similar to comment spam detection or email spam detection using keyword matching for typical spam words like viagra.
Some anti-virus softwares can maintain a log file about important files under Windows. The integrity information of those files are stored in their database and are recorded by check-summing. If a virus tries to modify a system file, the anti-virus software at once notifies the user by this technique.
The best part of this technique is, even if a system file gets corrupt (weirdly as it does sometimes without the initiative of Mr. virus) suddenly and tries to change and modify the boot sectors or say registry, the integrity of the files will be violated and the anti-virus will warn the user about that too.
Heuristic Scanning follows the behavioral pattern of a virus and has different set of rule for different viruses. If any file is observed to be following that set of particular activities then it infers that the particular file is infected. The most advanced part of Heuristic Scanning is that it can work against highly randomized polymorphic viruses too. Heuristic scanning technique has the potential to detect any future virus with ease. F-Secure Anti-virus quite successfully implements this technique.
This is the newest technique which continuously monitors your files for suspicious activities.
Imagine if a virus is hidden in a CD-ROM. Then how on earth would other anti-viruses come to know about it? But interceptors watches all external drives, data devices as well as internet download or even file download from email. That is why it provides real-time protection to your computer. When a virus comes from a DVD or a pen drive, be rest assured that an anti-virus software that has implemented interception technique will detect it immediately and warn you about it. Most of them will prevent you from running infected programs too.
The key feature of an interceptor is that it has to be very fast to avoid degrading user experience. But most of the modern day anti-virus software implementing the technique do it fairly well like for example Nod 32. NAV was at one time known to slow down your computer due to sluggish performance in interception. I heard it has improved over the years.
Thanks for reading so far. The two most important take home lessons are:
As you have reached the heart of the matter, you may want to take a look at this as well. A detailed free Windows anti-virus software here.
Credit to: http://blog.taragana.com
| avast! Professional Edition 4.8 AVG Anti-Virus 8.0 AVIRA AntiVir Premium 8.1 BitDefender Antivirus 11 eScan Anti-Virus 9.0 ESET NOD32 Anti-Virus 3.0 F-Secure Anti-Virus 2009 G DATA AntiVirusKit (AVK) 2009 Kaspersky Anti-Virus 2009 McAfee VirusScan Plus 12.1 Microsoft OneCare 2.5 Norman Antivirus & Anti-Spyware 7.1 Sophos Endpoint Protection 7.5.1 Symantec Norton Anti-Virus 2009 TrustPort Antivirus Workstation 2.8 VBA32 Scanner for Windows 3.12.8.2 |
 Internet Explorer 7.0 is the long awaited tabbed web browser by Microsoft. Nearly four years after the release of Internet Explorer 6.0, in the face of growing competition from Mozilla's Firefox, Microsoft has finally given the old IE platform a facelift. Optimized design along with new cool interface, favorites centre, search box, RSS feeds and most importantly easy to use tabbed browsing are the exclusive features of this new internet explorer.
Internet Explorer 7.0 is the long awaited tabbed web browser by Microsoft. Nearly four years after the release of Internet Explorer 6.0, in the face of growing competition from Mozilla's Firefox, Microsoft has finally given the old IE platform a facelift. Optimized design along with new cool interface, favorites centre, search box, RSS feeds and most importantly easy to use tabbed browsing are the exclusive features of this new internet explorer.
 But there are some tricky steps through which you can install Windows Defender Final even in your pirated copy of windows XP bypassing the genuine windows validation. You just have to follow the following steps one by one:
But there are some tricky steps through which you can install Windows Defender Final even in your pirated copy of windows XP bypassing the genuine windows validation. You just have to follow the following steps one by one:

 and then select 'Drop Row'.
and then select 'Drop Row'.





 Microsoft Private Folder is a useful tool for you to protect your private data when your friends, colleagues, kids or other people share your PC or account. With this tool, you will get one password protected folder called My Private Folder in your account to save your personal files.
Microsoft Private Folder is a useful tool for you to protect your private data when your friends, colleagues, kids or other people share your PC or account. With this tool, you will get one password protected folder called My Private Folder in your account to save your personal files.


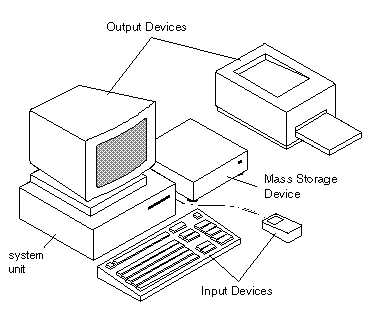
A computer system consists of different parts, programs or components. Each and every part has its own importance or working. In simple, we can say that hardware means all physical components of a computer and software is a set of certain instruction, rules on the basis of which other components work.
Software instructs a computer what to do. There are different types of programming languages, which make computing possible. There are three different types of computer software: system software, programming software and application software.
System software consists of programs that controls, integrates and looks after the hardware components of a computer system. It mainly consists of operating systems (OS), database management systems (DBMS), communications control programs, and programming language translator.
Programming software helps a user to write computer programs and other programming software languages in a proper way. The Application software will take care of different tasks other than just running the computer system.
Random access memory (RAM) is the computer memory in which computer software is loaded. There are different types of software available in the market. For e.g. Antispyware Software protect your computer data from virus. The software consistency mulls over the faults, mistakes and breakdown that are related with the formation and operation of computer software.
Author presents a website on software. This website provides information about meaning and types of computer software, working of computer software, layers of software in a computer system. You can visit his site to get information about computer softwares Article Source: http://EzineArticles.com/?expert=Mehar_Grewal |